Navigating the Incident Response Guide

Just released, the “Incident Response Guide” for the Water and Wastewater Sector, created by CISA, FBI, and EPA, is a comprehensive document designed to enhance cybersecurity resilience in this critical infrastructure sector. This guide provides detailed strategies and protocols for dealing with cyber incidents, emphasizing the importance of preparation, detection, analysis, containment, eradication, recovery, and post-incident activities. It outlines the roles and responsibilities of key federal partners, offers practical steps for building robust incident response plans, and stresses the significance of information sharing and collective response to cybersecurity threats.
Understanding the Threat Landscape
The first step in cybersecurity is understanding the threat landscape. Cyber threats are becoming more sophisticated, and as they evolve, so must our strategies to counter them. The Water and Wastewater Sector, critical to public health and safety, is particularly vulnerable. A breach here could lead to significant disruptions, hence the need for a comprehensive guide like the one developed by CISA, FBI, and EPA.
The Pillars of Cybersecurity Response
The guide lays out several pillars of an effective Water and Wastewater cybersecurity response:
1. Preparation and Prevention
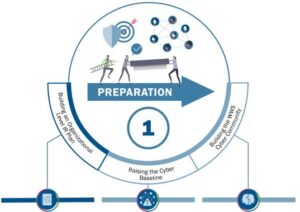
This is your first line of defense. It involves understanding your network’s architecture, identifying critical assets, and establishing baseline security measures. Regular employee training, cybersecurity drills, and a culture of security awareness form the bedrock of this phase.
2. Detection and Analysis
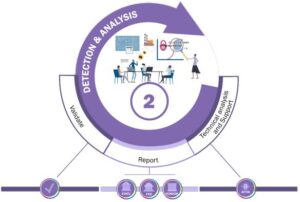
Here, the focus shifts to identifying and understanding the nature of the cyber threat. This involves monitoring systems for signs of a breach and having a robust mechanism in place for reporting and analyzing potential threats. Early detection is key to preventing widespread damage.
3. Containment, Eradication, and Recovery
Once a threat is identified, the next steps are to contain it, eradicate the malicious elements, and recover from the incident. This phase requires a swift and coordinated response to isolate affected systems, remove threats, and restore normal operations as quickly as possible.
4. Post-Incident Handling:
After an incident, it’s crucial to analyze what happened and why. This involves collecting and preserving data related to the incident, conducting a thorough analysis to understand the breach’s cause, and implementing measures to prevent future incidents. Learning from past incidents is invaluable in strengthening your cybersecurity posture.
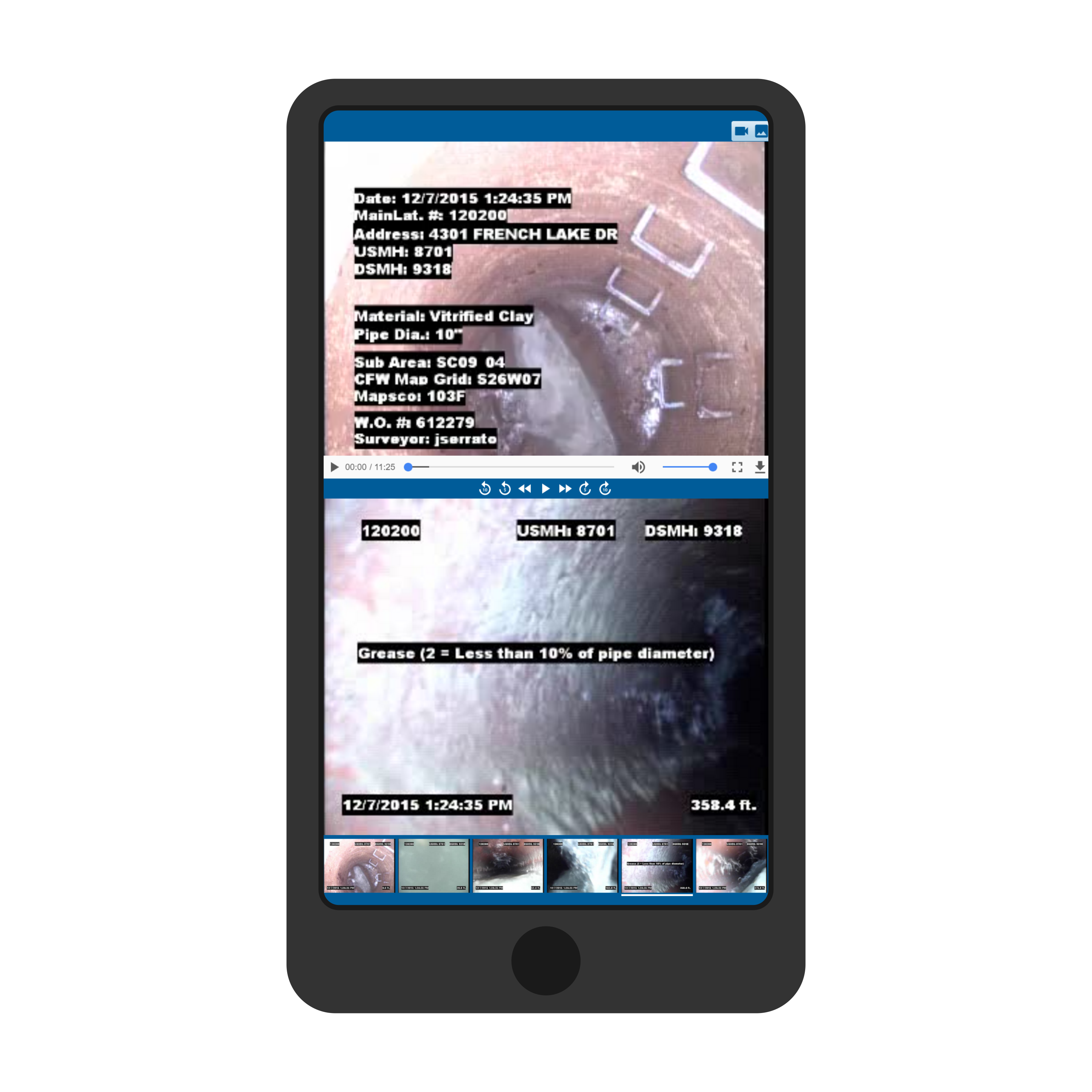
The Role of ITpipes in Enhancing Security
Now, let’s talk about how ITpipes play a crucial role in enhancing Water and Wastewater Cybersecurity. Cloud hosting with ITpipes isn’t just about storing data; it’s about creating a secure, resilient, and easily accessible environment for your critical infrastructure data. Here’s why this matters:

1. Enhanced Security Features
Cloud hosting with ITpipes offers advanced security features that protect your pipe inspection data from cyber threats. This includes encryption, regular security updates, and robust access controls.
2. Expertise and Support
With ITpipes, you don’t just get a service; you get a partnership. Our team of experts continually monitors potential threats and is ready to assist in implementing the best security practices.
3. Scalability and Accessibility
Cloud hosting allows for flexibility and scalability. As your data needs grow, ITpipes ensures that your infrastructure can handle this growth without compromising on security.
4. Data Backup and Recovery
In the unfortunate event of a data breach or loss, having your data hosted in the cloud means there’s always a backup available. Quick data recovery is essential in minimizing the impact of a cyber incident.
A Call to Action
In conclusion, the “Incident Response Guide” is a crucial tool in our arsenal against cyber threats, especially in the sensitive Water and Wastewater Sector. However, the guide is just the beginning. Implementing its recommendations and partnering with a trusted provider like ITpipes can bolster your cybersecurity posture.
As IT professionals, we have a responsibility to stay ahead of threats and protect our critical infrastructure. By understanding the guide’s principles and leveraging solutions like ITpipes’ cloud hosting, we can create a more secure and resilient digital infrastructure. Contact ITpipes today to learn how we can help you navigate the complex world of cybersecurity and ensure your data is safe, secure, and accessible.
To download the complete guide, click here.
To download ITpipes’ editorial “ITpipes Cloud – What’s the best option for you”, click here.
Similar blog posts: